Order Form
Going to the Discover app we can query for a winlog.event_data.TargetFilename value of C:\Users\lab-admin\Downloads\order\offer ordermgr.exe. This identifies the image C:\Users\lab-admin\Downloads\order\offer order.exe with a process ID (PID) of 9096. If we create a filter for the PID 9096, and disable our TargetFilename filter, we’ll get the process create for offer order.exe. The process create shows that offer order.exe was launched by 4358d11a-wsw10\lab-admin at 2020-10-18T00:14:07.737Z on 4358d11a-wsw10.windomain.local.
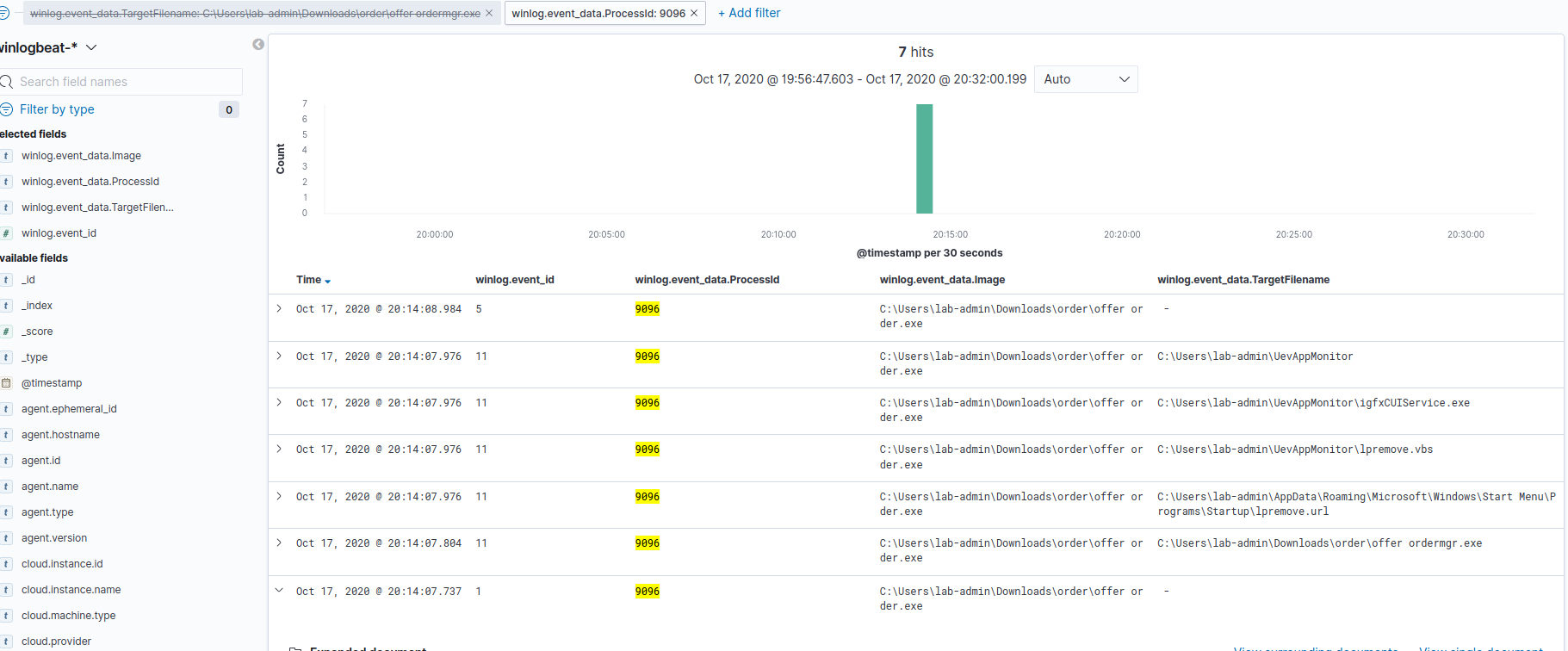
Let’s dig a little further and see what the original source of offer order.exe was.
To do that, we’ll follow the same steps that we did for offer ordermgr.exe. First, we’ll do a query in Discover to find a log that contains the winlog.event_data.TargetFilename value C:\Users\lab-admin\Downloads\order\offer order.exe. This will identify an Explorer process with PID 5800.
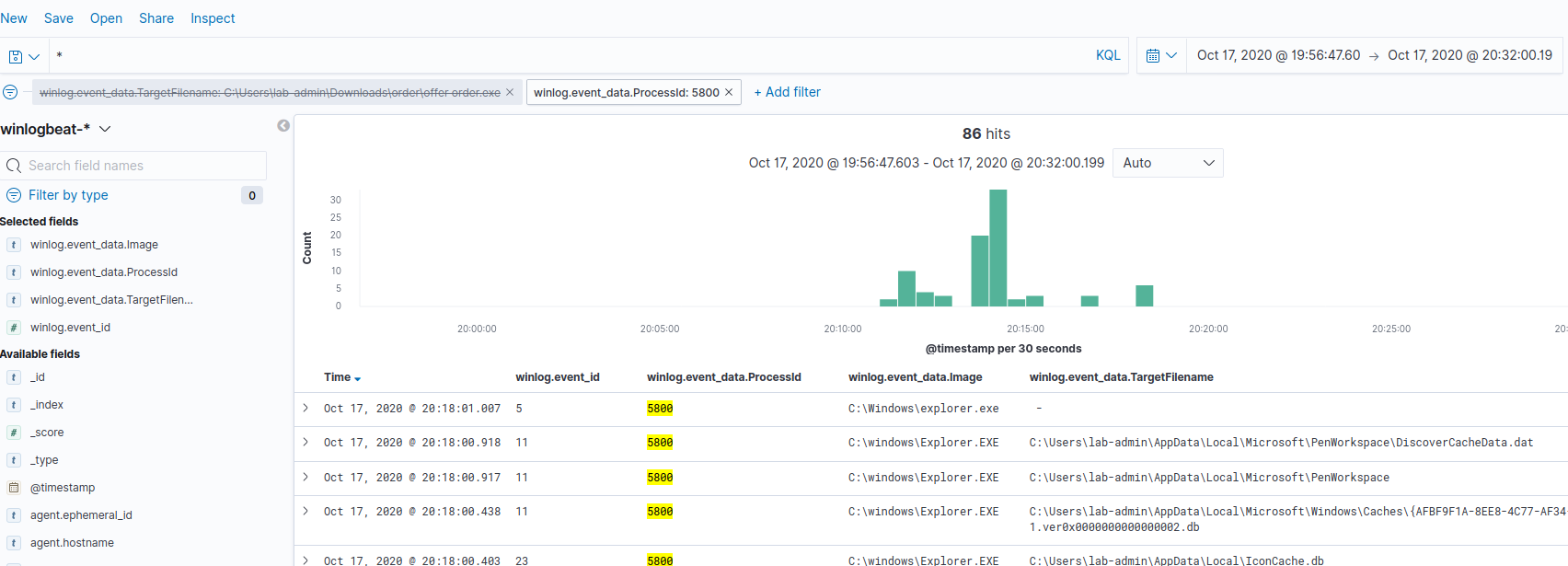
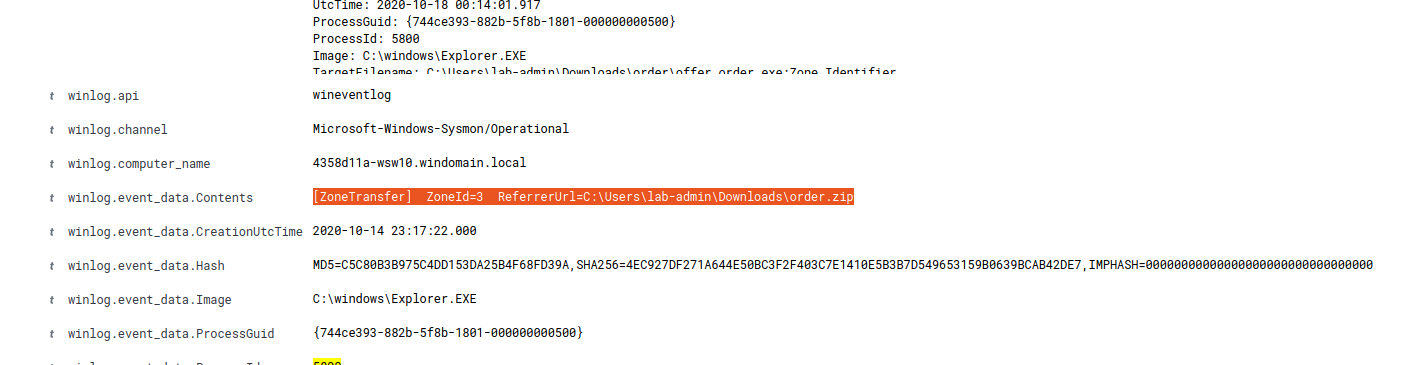
If we filter on PID 5800 and remove the TargetFilename filter, we can get the other events associated to that process. Looking at the results, there are some file create stream hash events (event ID 15), that contain our offer order.exe file with the Zone.Identifier string. At a high level, the Zone Identifier is used as a method to determine where a downloaded file came from. Expanding the records, you should be able to find a winlog.event_data.Contents value of [ZoneTransfer] ZoneId=3 ReferrerUrl=C:\Users\lab-admin\Downloads\order.zip, which is our original file.
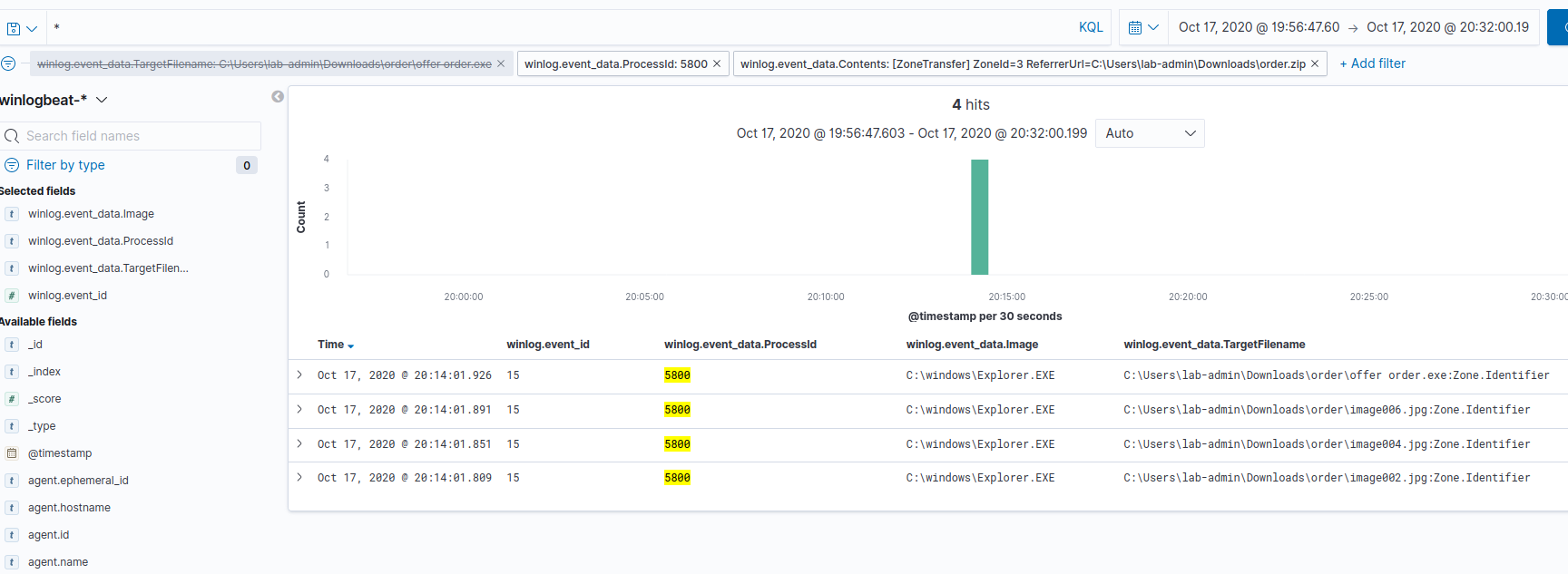
We can futher filter on all events that had the same winlog.event_data.Contents value to see the following files also came from that zip:
C:\Users\lab-admin\Downloads\order\image006.jpgC:\Users\lab-admin\Downloads\order\image004.jpgC:\Users\lab-admin\Downloads\order\image002.jpg
Going back to the events associated with PID 9096, we can see there was a file create (event ID 11) with the target filename C:\Users\lab-admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\lpremove.url at 2020-10-18T00:14:07.976Z. This means that on boot or logon, lpremove.url will be run.
Something worth noting is that you won’t actually see lpremove.url execute after the machine reboots (you can verify a reboot did happen thanks to an event ID 13 in the System logs at 2020-10-18T00:18:10.962Z and then an event ID 12 at 2020-10-18T00:18:20.681Z). Instead, this file is actually a shortcut initiating "C:\windows\System32\WScript.exe" "C:\Users\lab-admin\UevAppMonitor\lpremove.vbs", which does get captured.
Looking at the events associated to PID 9096, we see the following files were created:
- 2020-10-18T00:14:07.804Z
- Target Filename: C:\Users\lab-admin\Downloads\order\offer ordermgr.exe
- 2020-10-18T00:14:07.976Z
- Target Filename: C:\Users\lab-admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\lpremove.url
- 2020-10-18T00:14:07.976Z
- Target Filename: C:\Users\lab-admin\UevAppMonitor
- Note: This is a directory.
- 2020-10-18T00:14:07.976Z
- Target Filename: C:\Users\lab-admin\UevAppMonitor\lpremove.vbs
- 2020-10-18T00:14:07.976Z
- Target Filename: C:\Users\lab-admin\UevAppMonitor\igfxCUIService.exe
Other related files include order.zip and the various JPGs that we identified in the second question.
If we look at VT Hunting, we can see at the top of the VT Malicious Domains table there is a hit on a joomlas123 domain from explorer.exe. We could pin a filter on explorer.exe, but because it’s a legitimate process that will show up frequently, we’re likely going to get a lot of noise. Instead, we’ll pin the QueryName value, and pivot to Discover to find the PID of the specific explorer.exe making the request.
Taking this approach, we identify PID 6348 as the source. If we combine that PID with a filter on event ID 22 (for DNS queries), we can see it’s actually making a number of suspicious requests.
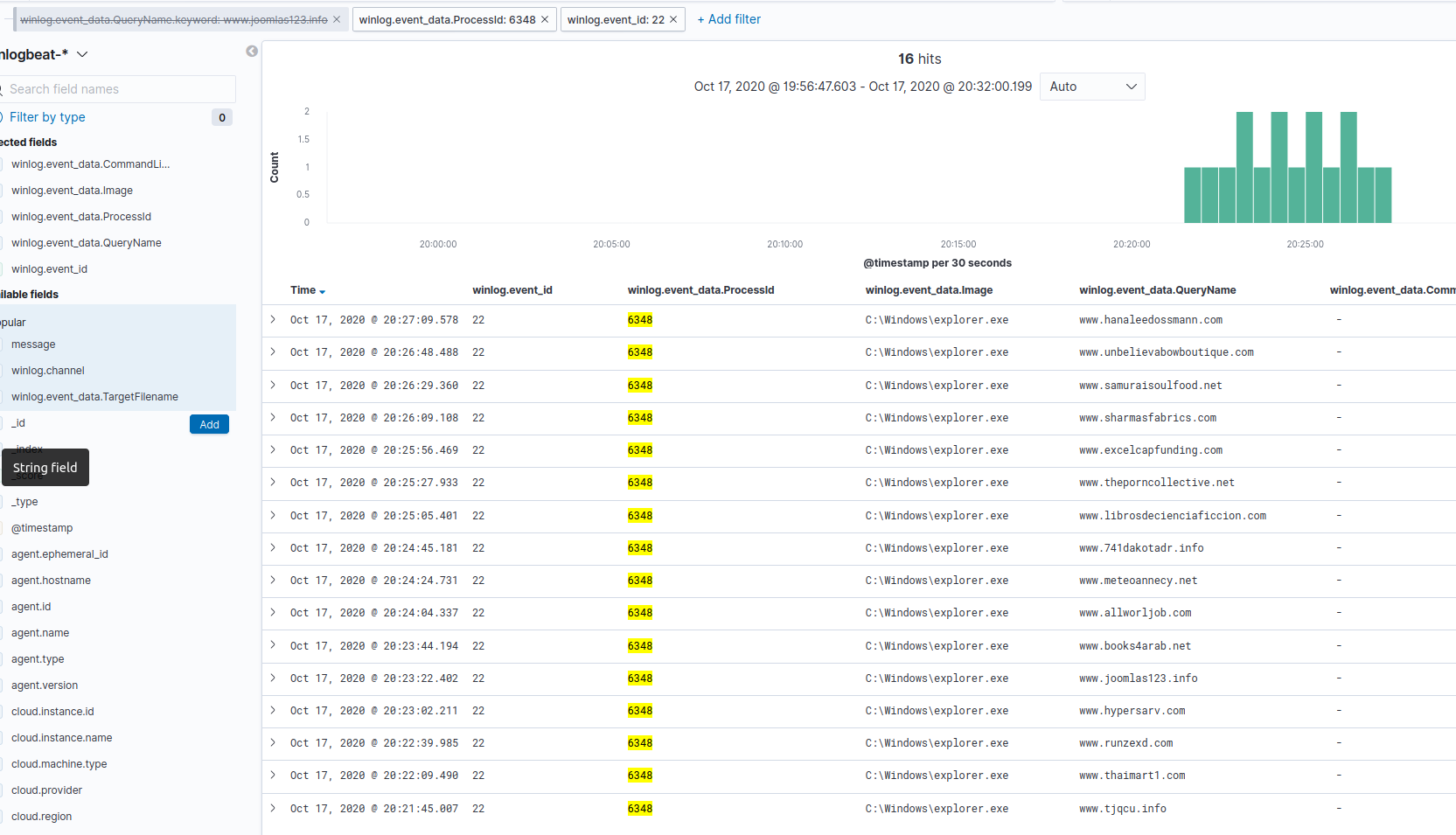
A bit of a spoiler, but if we dig further into the logs we have, we aren’t going to find a direct link to any of the previously identified files and this Explorer activity, other than a somewhat close proximity in time.
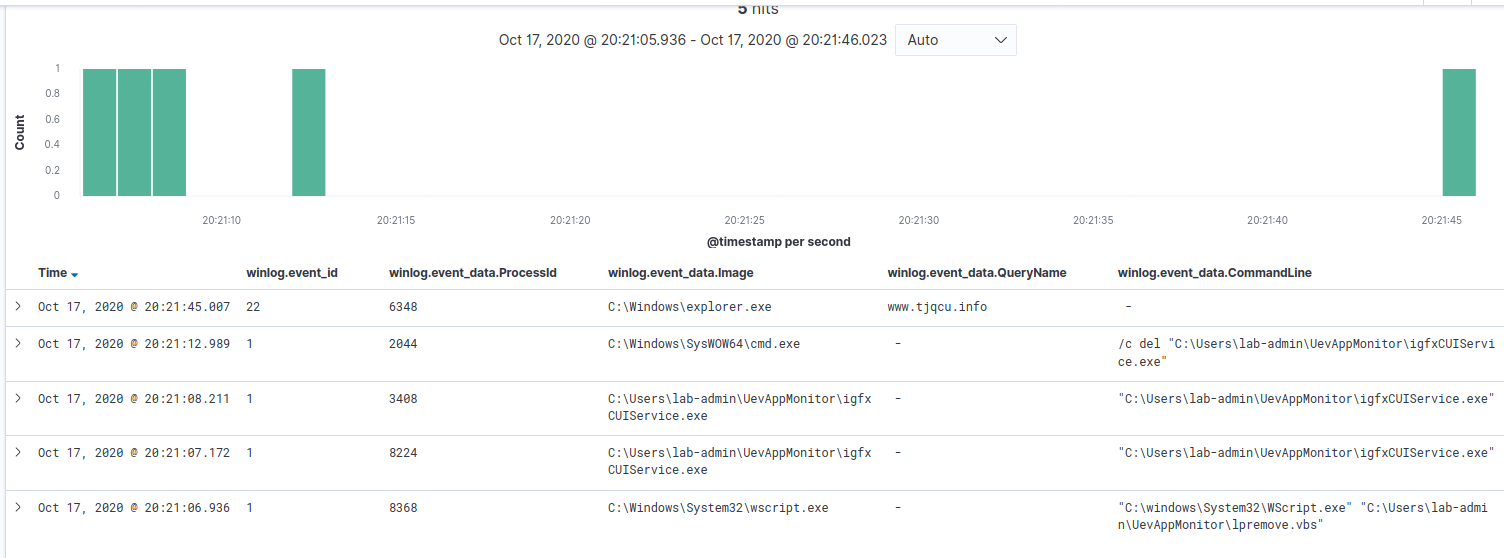
Sysmon process access (event ID 10) and create remote thread (event ID 8) are geared toward catching the causes of this kind of behavior. However, if not properly tuned, they can generate a lot of logs and have performance impacts on the endpoint you’re monitoring (this applies more to process access than create remote thread).
As great as it would be to log all of the things and store them indefinitely, in most organizations it just isn’t feasible. Plus, you’re likely to overwhelm yourself with noise that you won’t look at anyways. Instead, you’ll have to find a balance between your detection capability, and potentially missing certain steps of a compromise.
In this particular case, even if you don’t know exactly what caused explorer.exe to exhibit its behavior, it warrants a deeper dive on that machine (especially when combined with the other things we’ve found in this lab). One option could be to get copies of the files you identified and conduct static and dynamic analysis on them.
